服务人员¶
服务台的代理和访问管理应该很容易。在添加、编辑、使访问无效以及快速概览用户拥有哪些权限方面的灵活性将帮助您维护一个干净的权限系统,并在OTR中记录您的设置。
OTRS帮助您跨多个后端管理OTRS内的服务人员。 OTRS可以使用最多十个后端源,甚至将一些标记为只读。 集中管理用户设置,管理员可以快速使受感染的帐户无效,或者在出现意外疾病时将帐户设置为外出。
使用此屏幕将服务人员添加到系统。 默认情况下,新的OTRS安装包含具有管理员权限的服务人员。 服务人员管理屏幕位于 用户、组和角色 组的 服务人员 模块中。
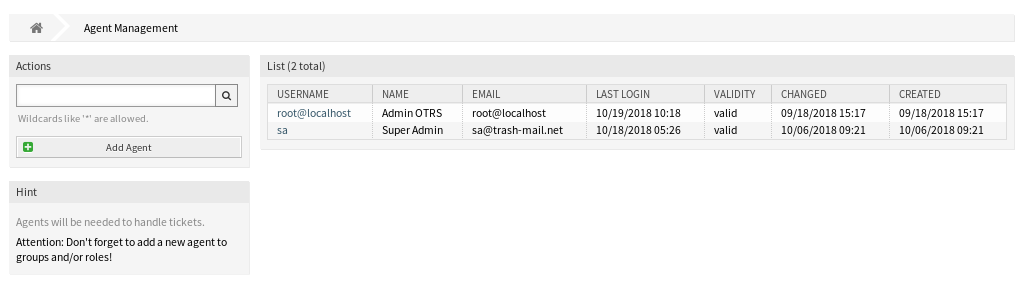
服务人员管理屏幕
警告
超级用户帐户用户名是 root@localhost。 不要使用超级用户帐户来使用OTRS! 创建新服务人员并改为使用这些帐户。 其中一个不利影响是 访问控制列表(ACL) 对超级用户无效。
管理服务人员¶
注解
只有使用数据库后端才能添加或编辑服务人员。使用LDAP之类的显式外部目录服务,并且根据配置,某些数据库是只读的。个人偏好(如外出)仍然可以设置。
若要添加一个服务人员:
- 点击左侧边栏中的 添加服务人员 按钮。
- 填写必填字段。
- 点击 保存 按钮。
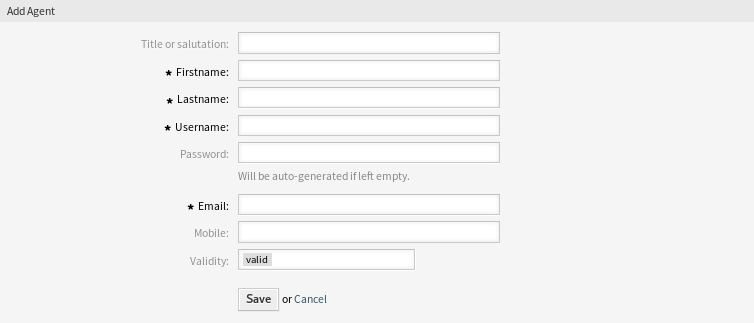
添加服务人员屏幕
警告
无法从系统中删除服务人员。 只能通过将 有效性 选项设置为 无效 或 临时无效 来停用它们。
若要编辑一个服务人员:
- 点击服务人员列表中的一个服务人员。
- 修改字段。
- 点击 保存 或 保存并完成 按钮。
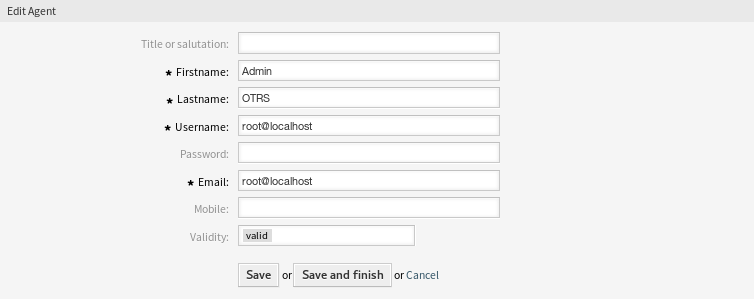
编辑服务人员屏幕
还可以编辑该服务人员的个人首选项。 要执行此操作,请单击 编辑服务人员 屏幕左侧边栏中的 编辑这个服务人员的个人首选项 按钮。
若要查找一个服务人员:
- 在左侧边栏的搜索框中输入搜索字词。
- 单击字段右侧的放大镜图标或敲击一下
回车键。
注解
如果系统中添加了多个服务人员,请使用搜索框查找特定服务人员。 默认情况下仅列出前1000个服务人员。
可以通过将服务人员添加到 组 或 角色 来控制服务人员权限。这可能导致权限的复杂矩阵。可以在 编辑服务人员 屏幕底部检查服务人员的有效权限。如果使用角色(推荐),则此屏幕将反映由角色指定的组合权限。
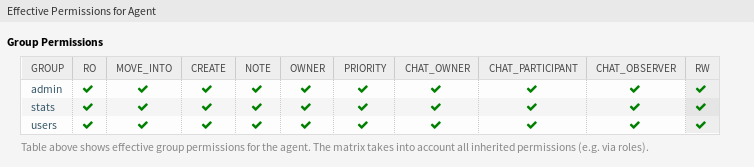
服务人员的有效权限小部件
服务人员设置¶
添加或编辑此资源时,可以使用以下设置。 标有星号的字段是必填字段。
注解
这些是可用于内部数据库表的默认字段。
- 头衔或问候语
- 可以在此处添加一些名称前缀,如 Mr.、Dr.、Jr. 等。
- 名 *
- 服务人员的名字部分。
- 姓 *
服务人员的姓。
参见
可以通过系统配置设置
FirstnameLastnameOrder设置服务人员显示名称。- 用户名 *
- 登录系统的服务人员的用户名。
- 密码
- 服务人员的密码。 如果留空,将自动生成。
- Email *
服务人员的邮件地址.
注解
The email syntax and validity of an available MX record could prevent you from submitting this form. For some systems it may be acceptable to turn off these checks.
- 手机
- 服务人员的手机号码。
- 有效性 *
- 设置此资源的有效性。 如果此字段设置为 有效,则每个资源即可仅在OTRS中使用。 将此字段设置为 无效 或 临时无效 将禁止此资源的使用。
Agent Back Ends¶
可以从Active Directory®或LDAP服务器读取和同步服务人员。
The administrator interface does not support the configuration of external back ends. Administrators need to edit the file Kernel/Config.pm by copying and pasting code snippets from Kernel/Config/Defaults.pm manually in case of using On-Premise system.
If you already have agent back end (e.g. SAP), it is possible to write a module that uses it.
警告
不要修改 Kernel/Config/Defaults.pm 文件,在升级升级后它会被覆盖!而是复制并粘贴代码片段到 Kernel/Config.pm 文件中。
注解
This feature is only available to On-Premise customers. If you are a Managed customer, this feature is taken care of by the Customer Solutions Team in OTRS. Please contact us via support@otrs.com or in the OTRS Portal.
Agent Back End - Database¶
The default user authentication back end for agents is the OTRS database. With this back end, all agent data can be edited via the administrator interface.
# This is the auth. module against the otrs db
$Self->{AuthModule} = 'Kernel::System::Auth::DB';
# defines AuthSyncBackend (AuthSyncModule) for AuthModule
# if this key exists and is empty, there won't be a sync.
# example values: AuthSyncBackend, AuthSyncBackend2
# $Self->{'AuthModule::UseSyncBackend'} = '';
# password crypt type (bcrypt|sha2|sha1|md5|apr1|crypt|plain)
# $Self->{'AuthModule::DB::CryptType'} = 'sha2';
# If "bcrypt" was selected for CryptType, use cost specified here for bcrypt hashing.
# Currently max. supported cost value is 31.
# $Self->{'AuthModule::DB::bcryptCost'} = 12;
Agent Back End - LDAP¶
If you have an LDAP directory with all your agent data, you can use the LDAP module to authenticate your agents. Because this module has only read-access to the LDAP back end, it is not possible to edit the agent data via the administrator interface.
# This is an example configuration for an LDAP auth. backend.
# (take care that Net::LDAP is installed!)
# $Self->{AuthModule} = 'Kernel::System::Auth::LDAP';
# $Self->{'AuthModule::LDAP::Host'} = 'ldap.example.com';
# $Self->{'AuthModule::LDAP::BaseDN'} = 'dc=example,dc=com';
# $Self->{'AuthModule::LDAP::UID'} = 'uid';
# Check if the user is allowed to auth in a posixGroup
# (e. g. user needs to be in a group xyz to use otrs)
# $Self->{'AuthModule::LDAP::GroupDN'} = 'cn=otrsallow,ou=posixGroups,dc=example,dc=com';
# $Self->{'AuthModule::LDAP::AccessAttr'} = 'memberUid';
# for ldap posixGroups objectclass (just uid)
# $Self->{'AuthModule::LDAP::UserAttr'} = 'UID';
# for non ldap posixGroups objectclass (with full user dn)
# $Self->{'AuthModule::LDAP::UserAttr'} = 'DN';
# The following is valid but would only be necessary if the
# anonymous user do NOT have permission to read from the LDAP tree
# $Self->{'AuthModule::LDAP::SearchUserDN'} = '';
# $Self->{'AuthModule::LDAP::SearchUserPw'} = '';
# in case you want to add always one filter to each ldap query, use
# this option. e. g. AlwaysFilter => '(mail=*)' or AlwaysFilter => '(objectclass=user)'
# or if you want to filter with a locigal OR-Expression, like AlwaysFilter => '(|(mail=*abc.com)(mail=*xyz.com))'
# $Self->{'AuthModule::LDAP::AlwaysFilter'} = '';
# in case you want to add a suffix to each login name, then
# you can use this option. e. g. user just want to use user but
# in your ldap directory exists user@domain.
# $Self->{'AuthModule::LDAP::UserSuffix'} = '@domain.com';
# In case you want to convert all given usernames to lower letters you
# should activate this option. It might be helpful if databases are
# in use that do not distinguish selects for upper and lower case letters
# (Oracle, postgresql). User might be synched twice, if this option
# is not in use.
# $Self->{'AuthModule::LDAP::UserLowerCase'} = 0;
# In case you need to use OTRS in iso-charset, you can define this
# by using this option (converts utf-8 data from LDAP to iso).
# $Self->{'AuthModule::LDAP::Charset'} = 'iso-8859-1';
# Net::LDAP new params (if needed - for more info see perldoc Net::LDAP)
# $Self->{'AuthModule::LDAP::Params'} = {
# port => 389,
# timeout => 120,
# async => 0,
# version => 3,
# };
# Die if backend can't work, e. g. can't connect to server.
# $Self->{'AuthModule::LDAP::Die'} = 1;
连接目录服务器所必需的最少信息是:
$Self->{AuthModule} = 'Kernel::System::Auth::LDAP';
$Self->{'AuthModule::LDAP::Host'} = 'ldap.example.com';
$Self->{'AuthModule::LDAP::BaseDN'} = 'dc=example,dc=com';
$Self->{'AuthModule::LDAP::UID'} = 'uid';
Host- 目录服务器的DNS名称或IP。
BaseDN- 目录树中的起点。
UID用于登录和识别的属性。
注解
对于Active Directory这里是
sAMAccountName。
It is possible to connect to an LDAP via secure connection. In this case the ldaps:// protocol has to be added to the host parameter and the port has to be changed.
$Self->{'AuthModule::LDAP::Host'} = 'ldaps://secure.example.com';
$Self->{'AuthModule::LDAP::Params'}->{port} = 636;
要使用多个后端,请继续将示例代码添加到 Config.pm 的其它部分。 请确保在所有设置后添加数值[1-9],以指示哪些设置属于哪个后端。
### Backend One
$Self->{AuthModule} = 'Kernel::System::Auth::LDAP';
$Self->{'AuthModule::LDAP::Host'} = 'ldap.example.com';
$Self->{'AuthModule::LDAP::BaseDN'} = 'dc=example,dc=com';
$Self->{'AuthModule::LDAP::UID'} = 'uid';
### Backend Two
$Self->{AuthModule1} = 'Kernel::System::Auth::LDAP';
$Self->{'AuthModule::LDAP::Host1'} = 'ldap.example.com';
$Self->{'AuthModule::LDAP::BaseDN1'} = 'dc=example,dc=com';
$Self->{'AuthModule::LDAP::UID1'} = 'uid';
警告
所有后端将连续使用。对于所有后端,UID都必须是唯一的,否则可能会产生一些副作用。
If an LDAP server is not available another one should be used as fallback. Since there is only one host setting in each back end configuration, the servers have to be added in an array.
$Self->{'AuthModule::LDAP::Host'} = ['ldaps://ldapserver_one.com', 'ldaps://ldapserver_two.com'];
$Self->{'AuthModule::LDAP::Die'} = 0;
Please note that there is no real fallback functionality but this workaround should work in most cases. The system will always try the first LDAP server first and after a timeout the second one. The recommended way is to configure a fallback or redundant LDAP at server side.
To synchronize with a specific directory server, you must add the appropriate setting to your agent authentication back end. To achieve this copy the following block from the Defaults.pm and paste it into the Config.pm.
$Self->{'AuthModule::UseSyncBackend'} = 'AuthSyncBackend';
要使用多个后端,请继续将示例代码添加到 Config.pm 的其它部分。 请确保在所有设置后添加数值[1-9],以指示哪些设置属于哪个后端。
$Self->{'AuthModule::UseSyncBackend1'} = 'AuthSyncBackend1';
Reuse of an agent synchronization back end is also possible.
$Self->{'AuthModule::UseSyncBackend1'} = 'AuthSyncBackend';
建议同步服务人员数据,以便在授权之前不必手动将服务人员添加到用户表中。此外,可以使用目录服务器的安全对象自动添加组和角色。
注解
Multiple agent synchronization back end blocks can be used. Please make sure to add a numeric value [1-9] to all settings to indicate which settings belong to which back end. Each AuthSyncModule must be explicitly used in an agent authentication back end.
登录时同步用户数据。要实现此操作,请复制 Defaults.pm 中的以下内容并将其粘贴到 Config.pm 中。
# This is an example configuration for an LDAP auth sync. backend.
# (take care that Net::LDAP is installed!)
# $Self->{AuthSyncModule} = 'Kernel::System::Auth::Sync::LDAP';
# $Self->{'AuthSyncModule::LDAP::Host'} = 'ldap.example.com';
# $Self->{'AuthSyncModule::LDAP::BaseDN'} = 'dc=example,dc=com';
# $Self->{'AuthSyncModule::LDAP::UID'} = 'uid';
# The following is valid but would only be necessary if the
# anonymous user do NOT have permission to read from the LDAP tree
# $Self->{'AuthSyncModule::LDAP::SearchUserDN'} = '';
# $Self->{'AuthSyncModule::LDAP::SearchUserPw'} = '';
# in case you want to add always one filter to each ldap query, use
# this option. e. g. AlwaysFilter => '(mail=*)' or AlwaysFilter => '(objectclass=user)'
# or if you want to filter with a logical OR-Expression, like AlwaysFilter => '(|(mail=*abc.com)(mail=*xyz.com))'
# $Self->{'AuthSyncModule::LDAP::AlwaysFilter'} = '';
# AuthSyncModule::LDAP::UserSyncMap
# (map if agent should create/synced from LDAP to DB after successful login)
# you may specify LDAP-Fields as either
# * list, which will check each field. first existing will be picked ( ["givenName","cn","_empty"] )
# * name of an LDAP-Field (may return empty strings) ("givenName")
# * fixed strings, prefixed with an underscore: "_test", which will always return this fixed string
# $Self->{'AuthSyncModule::LDAP::UserSyncMap'} = {
# # DB -> LDAP
# UserFirstname => 'givenName',
# UserLastname => 'sn',
# UserEmail => 'mail',
# };
连接目录服务器所必需的最少信息是:
$Self->{AuthSyncModule} = 'Kernel::System::Auth::Sync::LDAP';
$Self->{'AuthSyncModule::LDAP::Host'} = 'ldap.example.com';
$Self->{'AuthSyncModule::LDAP::BaseDN'} = 'dc=example,dc=com';
$Self->{'AuthSyncModule::LDAP::UID'} = 'uid';
Host- 目录服务器的DNS名称或IP。
BaseDN- 目录树中的起点。
UID用于登录和识别的属性。
注解
对于Active Directory这里是
sAMAccountName。
Agent Back End - HTTPBasicAuth¶
If you want to implement a single sign on solution for all your agents, you can use HTTPBasic authentication (for all your systems) and use the HTTPBasicAuth module with OTRS. No login is needed with OTRS any more.
# This is an example configuration for an apache ($ENV{REMOTE_USER})
# auth. backend. Use it if you want to have a singe login through
# apache http-basic-auth.
# $Self->{AuthModule} = 'Kernel::System::Auth::HTTPBasicAuth';
# In case there is a leading domain in the REMOTE_USER, you can
# replace it by the next config option.
# $Self->{'AuthModule::HTTPBasicAuth::Replace'} = 'example_domain\\';
# In case you need to replace some part of the REMOTE_USER, you can
# use the following RegExp ($1 will be new login).
# $Self->{'AuthModule::HTTPBasicAuth::ReplaceRegExp'} = '^(.+?)@.+?$';
# Note:
# If you use this module, you should use as fallback the following
# config settings if user isn't login through apache ($ENV{REMOTE_USER}).
# $Self->{LoginURL} = 'http://host.example.com/not-authorised-for-otrs.html';
# $Self->{LogoutURL} = 'http://host.example.com/thanks-for-using-otrs.html';
注解
Multiple agent synchronization back end blocks can be used. Please make sure to add a numeric value [1-9] to all settings to indicate which settings belong to which back end. Each AuthModule must be explicitly used in an agent authentication back end.
Agent Back End - Radius¶
The settings shown in example below can be used to authenticate your agents against a Radius server.
# This is example configuration to auth. agents against a radius server.
# $Self->{'AuthModule'} = 'Kernel::System::Auth::Radius';
# $Self->{'AuthModule::Radius::Host'} = 'radiushost';
# $Self->{'AuthModule::Radius::Password'} = 'radiussecret';
# Die if backend can't work, e. g. can't connect to server.
# $Self->{'AuthModule::Radius::Die'} = 1;